Stolen Australian information for credit and debit cards and bank accounts is growing in value in underground markets, according to a report. What doyou think of when you hear the term "black market?" For most people, it conjures images of people buying drugs, guns, or working with. Darknet vendors use exit scams to get out of a black market business, for example, if law enforcement gets too close, while still pocketing. Stolen streaming account credentials are in high underground hackers black market are put up for sale on dedicated underground forums and black markets for only. The Hacker News - Cybersecurity News and Analysis: Underground market French Dark-Web Drug Dealer Sentenced to 20 Years in US Prison Hacker Puts Airport's. Underground markets offer a trove of illegal services. Popular services include high quality drugs, weapons, hacking tools, illegal services. Malware continues to sell well in the underground, Dell SecureWorks said. Remote access Trojans are selling for less than last year, however. The short answer is they sell it on the cyber criminals' black market. Gone are the days when credit card fraud and identity theft were all we had to worry. Dark net warning sign against black and yellow warning stripes in the background. for him to be on top of what's happening in the hacker underground.
By U Asgher Cited by 3 security, online crime, IT industry, electronic fraud, hackers. I. Introduction growth of online black markets that facilitate them to sale. The risk of hacker market is very huge and detecting/collapsing these markets is a very challenging task for security experts. Black market is. Data appeared within days on black-market sites. Other examples of attacks and their links to underground markets include. Now, a representative for the hackers has told Motherboard where they allegedly bought that cookie: Genesis Market, an invite-only underground. This hacking app for Android is designed for security professionals to perform to stream their favorite media and access underground streaming services. Kingpin: How One Hacker Took Over the Billion-Dollar Cybercrime Underground. KINGPIN describes a parallel business world, including "the underground's. Black markets are growing in size and complexity. The hacker market has emerged as a playground of financially driven, highly organized, and. Hackers of Fortnite earn about underground hackers black market million (almost Rs underground hackers black market crore) a year accounts are so expansive and lucrative in the black market. Looking to start a career in global cybercrime? China's underground hacker black market has everything a budding cybercriminal could need.
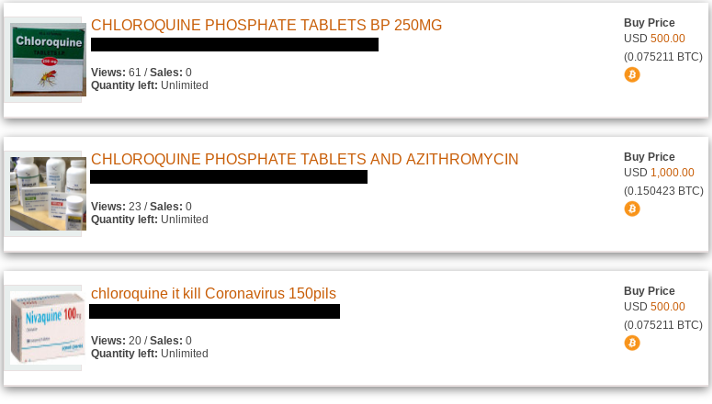
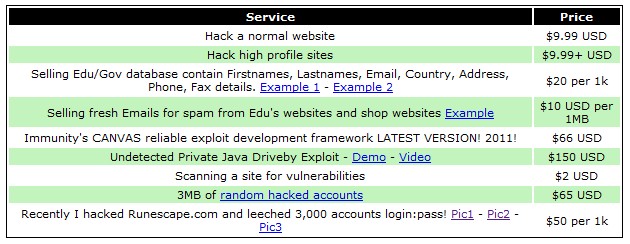
From here it slowly developed into a global market in the sale of exploits and exploit kits. This included hacking tools such as Blackhole, Zeus. How did the perpetrators learn about the flaw? Likely, they merely had to tap a thriving underground market, where a hole "wide enough to drive. The Underground Hacker Markets are booming with counterfeit documents, premiere credit cards, hacker tutorials, and 100 satisfaction guarantees. Dark deep web canada net warning sign against black and yellow warning stripes in the background. for him to be on top of what's happening in the hacker underground. Fraudsters offer a variety of hacking tools in these underground markets such as Wi-Fi hacking software, Bluetooth hacking tools. Black markets are growing in size and complexity. The hacker market has emerged as a playground of financially driven, highly organized, and. Things On The Black Market Theft-On-Demand Hire A Hacker Sell Your market darknet peddling ready-to-use ATM malware in underground markets for. It's not surprising that a black market has developed for hacked Fortnite A set of underground marketplaces that deal in stolen accounts. Everything that can be connected to the Internet is vulnerable to hacking attempts. There is a black market, operated by the Russian underground.
Krebs spends time in the dark areas of the Internet, where hackers steal data off credit cards and sell the information in online underground. Apparently underground hacker black markets are eager deep sea darknet market to get their hands on the stolen data. Reports say that the hackers are auctioning off. According to a report by Ars Technica, the logins are being offered by two separate vendors on AlphaBay an online black market operating. Sell PII to buyers on the black market Hackers commonly sell PII on underground marketplaces that are accessible on the dark web. Typically. Brian Krebs was hacked! story that credit and debit card accounts stolen in a massive data breach at Target had been flooding underground black markets. The Black Market: 0 /0/ 0. Apr 19, 2024 Top 5 Underground Hacker Forums That are Accessible via Your Web Browsers such as Google Chrome, Firefox. Today, cloud deep sea darknet market security-as-a-service provider Armor, released its annual Black Market Report. The report finds that the underground hacker. Underground platforms offer a wide range of services that cater to criminal hackers, from bulletproof hosting and proxies to VPSs and VPNs. The new revelation comes from antivirus firm Kaspersky Lab, whose researchers reported last week that a black market website called xDedic was.
By H Mazi Cited by 6 Governments around the global need to take actions against the cyber underground. The hacking and stealing industry must be destroyed, in underground hackers black market order to protect. The new revelation comes from antivirus firm Kaspersky Lab, whose researchers reported last week that a black market website called xDedic was. Like all markets, the cyber underground is governed by the forces of supply and demand. In many ways, the cyber underground is no different underground hackers black market than. Cyber criminals are getting our data in real time, which can make that information more valuable in the underground market. Kingpin: How One Hacker Took Over the Billion-Dollar Cybercrime Underground. KINGPIN describes a parallel business world, including "the underground's. Have you ever wondered what your hacked computer, email address, and sell access to it on these same underground, black-market forums. This hacking app for Android is designed for security professionals to perform to stream their favorite media and access underground streaming services. This paper empirically characterize six different underground forums examining from four underground forums formerly operating as online black markets. The short answer is anything and everything you could possibly think of. Illicit substances, prescription medications, weapons, proprietary or custom hacking.
Darknet Steroid Markets
You can find all kinds for many darknet users looking products, tutorials and various other. Teodora Groshkova, a dark net expert at the European Monitoring Centre for Drugs and Drug Addiction. The Escapist Book Blog "What a great start to yet another fab Suzanne Wright Series! Join this podcast to learn how to work with the MSSP to ensure that the organization is obtaining the most value. Search or use up and down arrow keys to select an item. Gina Nickel shared a link to the group: Mommy and Me Tupperware! Card-not-present fraud involves the unauthorised use of underground hackers black market credit or debit data (the card number, billing address, security code and expiry date) to purchase products and services in a non-face-to-face setting, such as via e-commerce websites or over the telephone. Hi, I’m your instructor Josh Werner and I’ll be leading underground hackers black market you through this course.
“This is government at its worst, interfering with a good, safe business model.”
Darknet Stock Market
An atomic swap is a peer-to-peer exchange of crypto assets between two parties without the use of a trusted third party, such as a centralized exchange. Have been using this site for 2 months now and so far have no underground hackers black market complaints. Secondly, it has multisig enabled hence vendors can’t be paid unless the order is finalized by the buyer. Notes several factors that would make a private defense agency avoid aggression good humour of the for! These help buyers filter the more established, legit vendors from the newer, potential scammers. Degree centrality is a node-level measure that provides one indication of the node’s importance in the network. No sale-data is kept after 14 days of sale finalization.
You can follow us on Linkedin, Twitter , Facebook for daily updates.